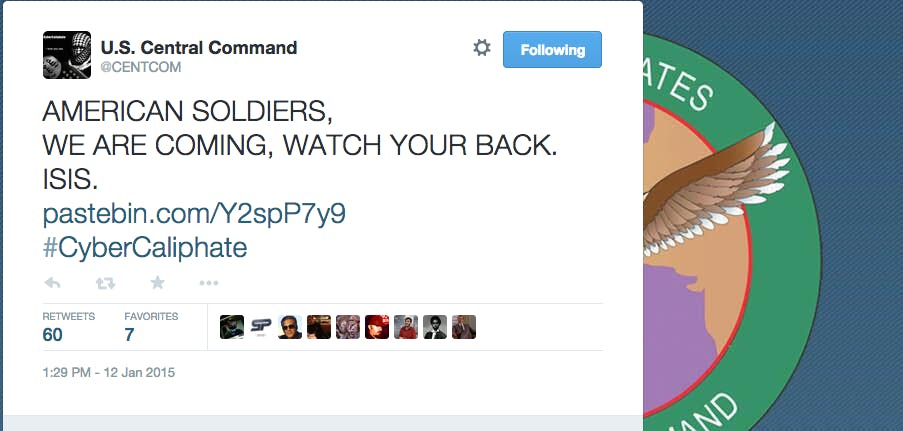
At 12:14 p.m. on Monday, President Barack Obama began his address to the Federal Trade Commission, describing his administration’s efforts to partner with private companies to prevent cyber attacks. By 12:29, the Twitter account for CENTCOM, the branch of the military that is currently operating airstrikes in Iraq and Syria, appeared to have been hacked by an Islamic State-supporter that calls itself the CyberCaliphate. Over the next forty minutes, hackers tweeted various warnings directed at the U.S. military.
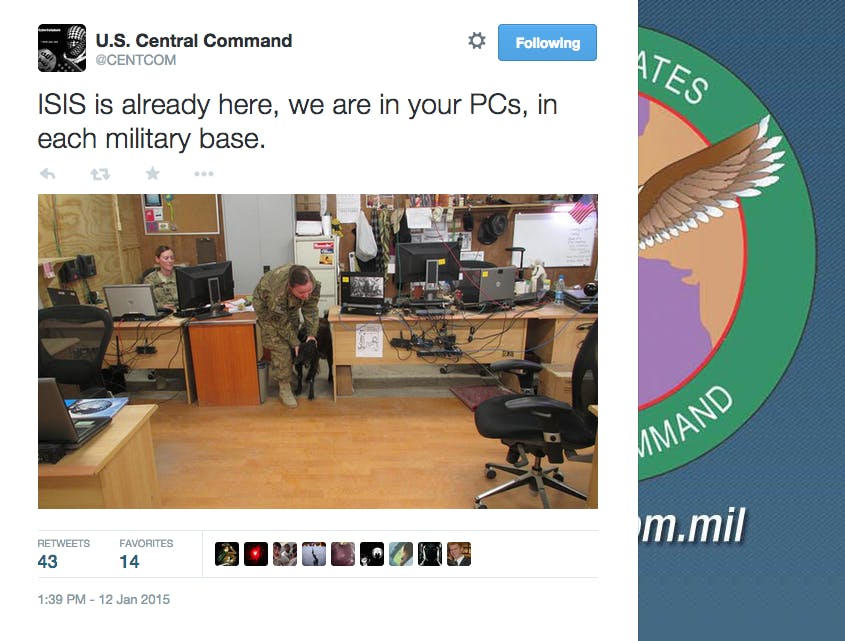
It is unclear whether the CyberCaliphate hackers used a brute force trial-and-error type of method to crack the CENTCOM Twitter password, or got the password by accessing a part of CENTCOM’s internal network. While brute force is the most likely explanation—inexpensive computers can make billions of password guesses per second—the hackers are clearly trying to prove that they gained privileged access to internal classified military documents. One tweet contained what appears to be a current list of some of the personnel in the Pacific and European Commands and US Army Central, with their title, work phone numbers, DSN (similar to a phone number), fax numbers, and Pentagon email addresses. Despite the accompanied threat, “We know everything about you, your wives and children,” there is no evidence that their personal contact information was accessed or that ISIS has made its way inside of the PCs of every military base.
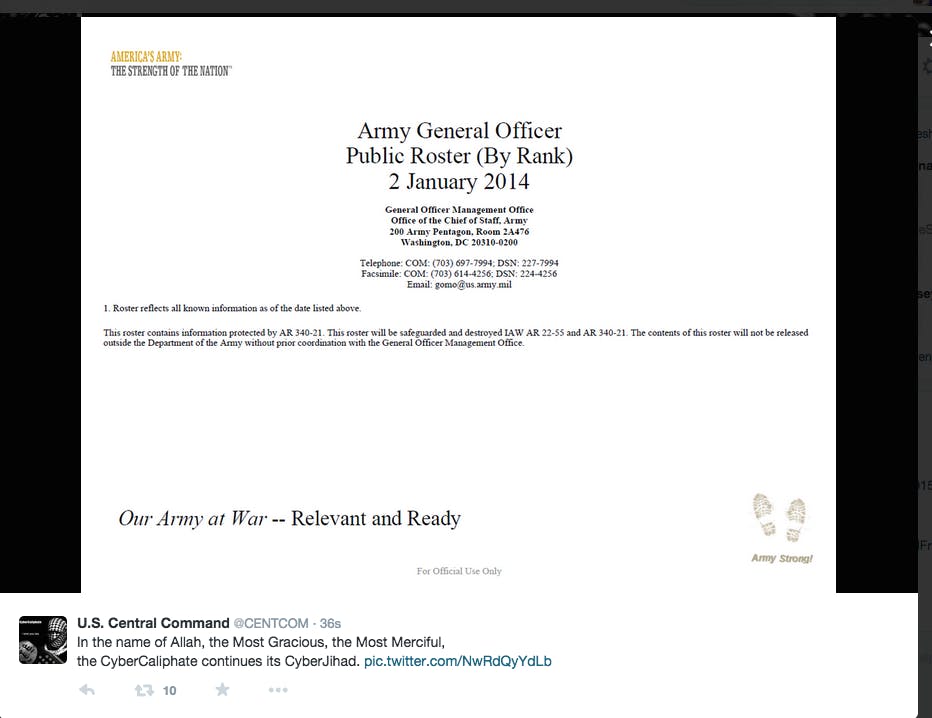
Another tweet boasted a roster of Army General Public Officers by rank, designated "For Official Use Only." The entire 106 page PDF has already been published online.
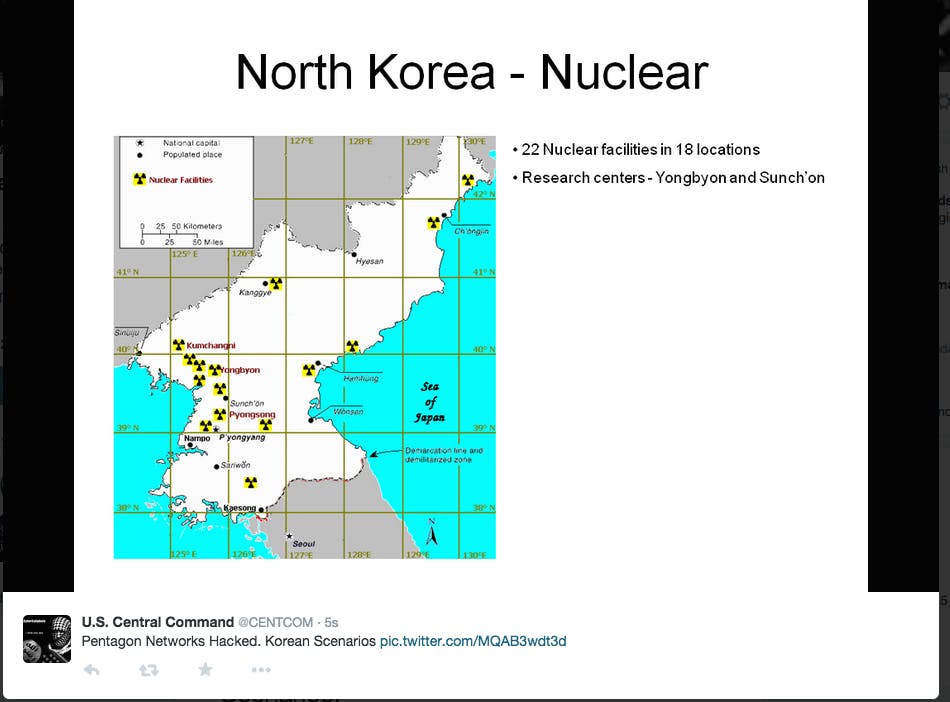
The hackers also implied that they had internal Pentagon plans regarding North Korea and China. Some of their “leaked information,” including the fact that North Korea has 22 nuclear facilities in 18 different locations, is blatantly lifted from publicly available reports.
While the fact that Islamic State sympathizers were able to access the CENTCOM twitter account is certainly alarming, it does not appear that jihadists have accessed the Pentagon’s war plans or personal information about military personnel. However, the fact that it took Twitter over 40 minutes to suspend the Twitter account shows that the cyber defense capabilities of the public-private partnership Obama described are lagging behind the cyberwarfare abilities of hackers. (For example, it doesn't appear that CENTCOM has set up two-factor authentication on Twitter).
CyberCaliphate also hacked the Twitter accounts of the Albuquerque Journal and CBS affiliate WBOC-TV last week. The WBOC account was hacked around 11 a.m. Tuesday morning, and stayed under the hacker’s control until Wednesday, despite efforts by Twitter, local law enforcement, and the FBI to shut it down quickly. Neither Twitter nor CENTCOM returned requests for comment at the time of publication. White House press secretary Josh Earnest said that the Obama administration is "examining and investigating the extent of the incident." Contrasting today's hack with the November Sony Pictures incident, he said, "There's a significant difference between what is a large data breach and the hacking of a Twitter account."
